Create Your Own Search Engines for Bug Bounty
In this blog, we will explore how to utilize Custom Search Engines effectively for Bug Bounties. Google’s Programmable Search Engine can be accessible at https://programmablesearchengine.google.com/, is a handy tool for searching specific keywords across all your targets. Similarly, Bing’s Custom Search Engine is available at https://www.customsearch.ai/. In this article, we will focus on Google Custom Search, and we will discuss Bing Custom Search in the upcoming article. Let’s first discuss what’s Google Programmable Search Engine (GPSE) or Custom Search Engine (CSE).
What is Google Programmable Search Engine or Custom Search Engine (CSE)?
Google Programmable Search Engine is a platform provided by Google enables you to create a search engine for your target website to help your visitors find the information they are looking for. You must have seen this kind of search bar in many websites, these are the search engines provided by Google.
This lets you create your own search engine. The only thing you need to do is simply choose which websites you want to search, and that’s it.
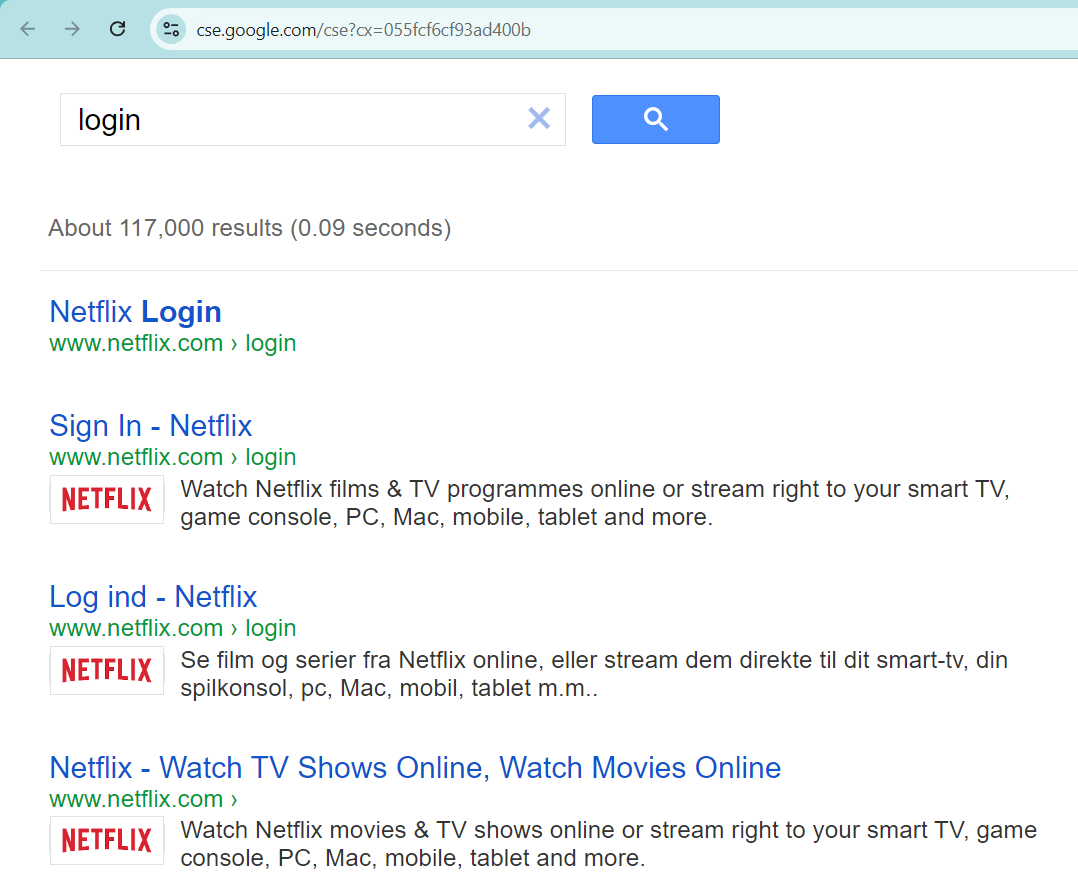
For example, if we want to search for videos exclusively on YouTube and Dailymotion, we simply need to use a Programmable Search Engine (GPSE) or Custom Search Engine (CSE). We would set YouTube as site 1 and Dailymotion as site 2. Once configured, Google will provide us with a link to this custom search engine. Any search we perform using this link will only return results from YouTube and Dailymotion, excluding other websites.
Creating Your Custom Search Engine for Bug Bounty Targets
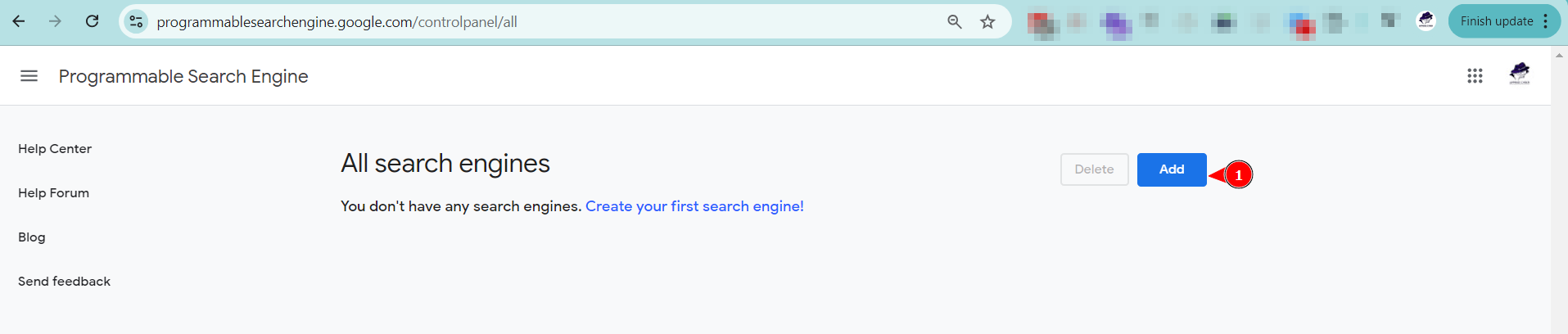
Visit the Google Programmable Search Engine Website
Sign In
- Using the “Sign in” button in the top right corner, log in with your Google account.
Start Creating a New Search Engine
- When you click on “add,” you will be able to name and start your search engine.
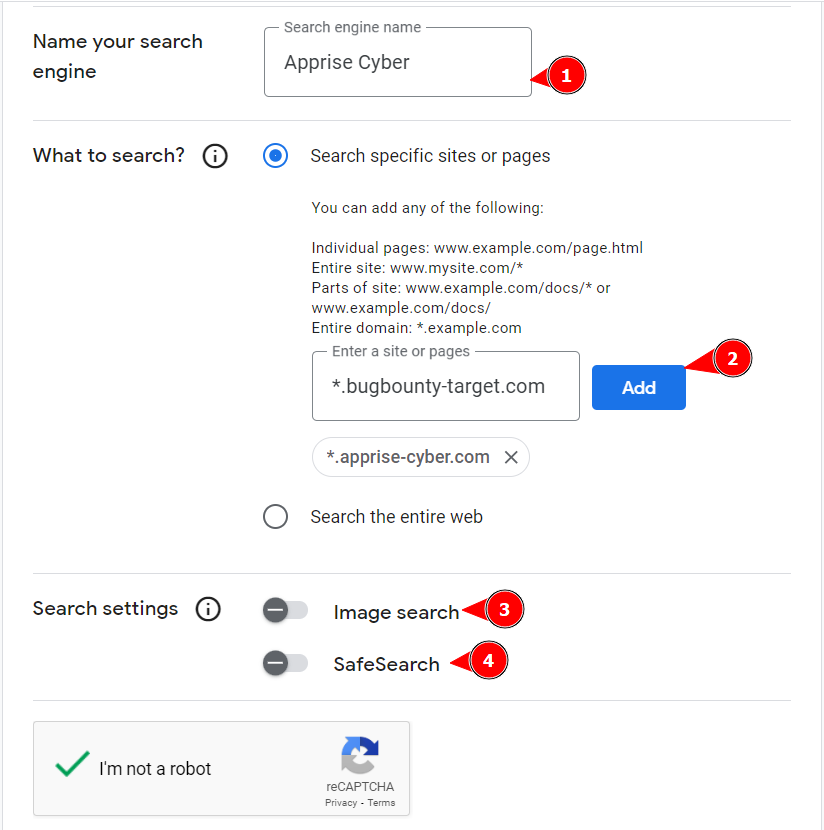
Configure Your Search Engine
- Name Your Search Engine: Choose a descriptive name that reflects its purpose, such as “Bug Bounty Targets Search Engine.”
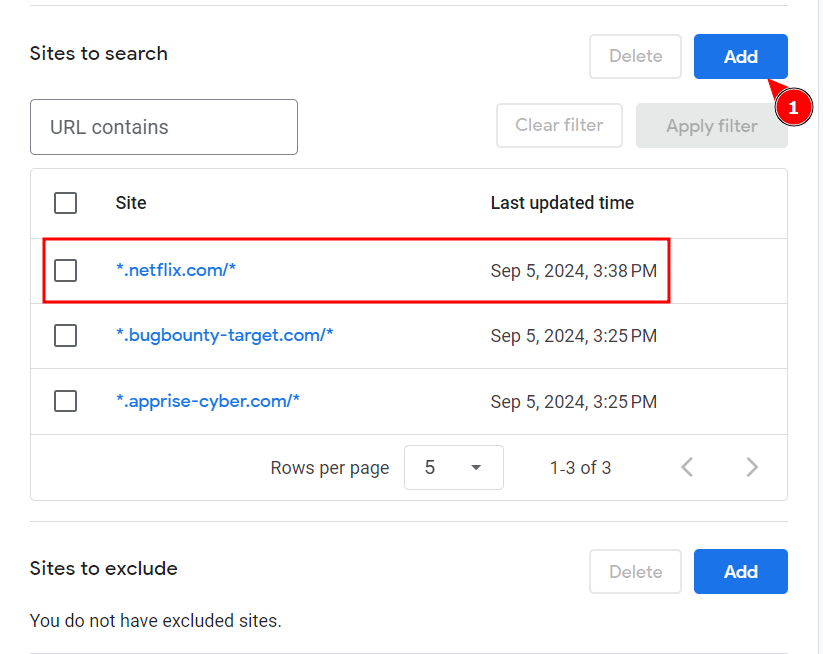
- Sites to Search: Enter the URLs of your bug bounty targets or specific domains you want to focus on. For example, if you’re targeting specific subdomains or sites relevant to your bug bounty research, list them here.
Note: When creating your search engine for the first time, we recommend including at least one wildcard domain.
- You can leave the image search and safe search options unchecked as these filters may restrict your results unnecessarily. Once you have done that, complete the CAPTCHA and click “Create” to finalize the setup.
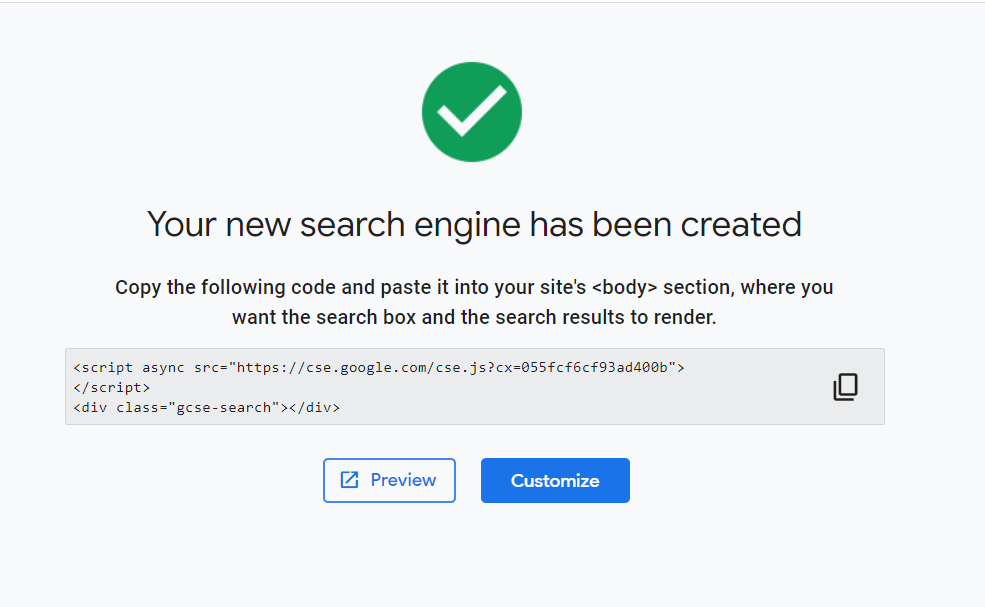
Create
- Once you have configured your search engine, click the “Create” button. Google will generate a custom search engine tailored to your bug bounty targets.
Note: If the site is owned by you, insert the provided code into the `<body>` section of your site to embed the search box and display the search results. However, this is not our focus for today.
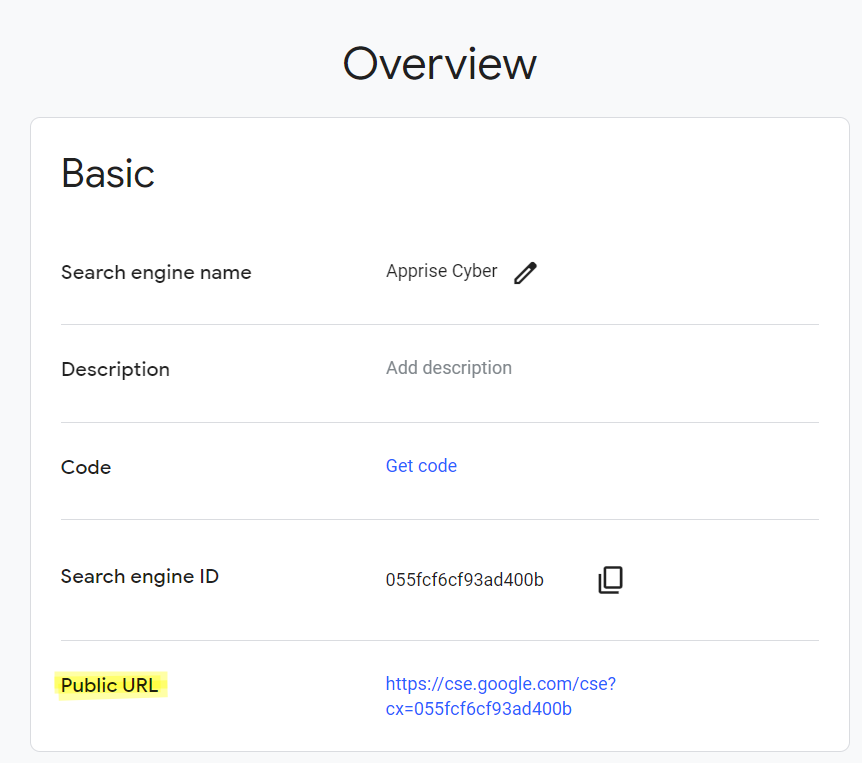
Get Your Search Engine Link
- You will receive a link after creation to your custom search engine. Now, click on “Customize” You can use a public URL of your search engine This link will lead to a search page that only includes the domains and sites you have specified.
Customize Further (Optional)
- You can further customize the search engine’s appearance and functionality through the control panel provided by Google, making it even more suited to your bug bounty research. For Example, we can add as many targets as we can. we recommend using the BBSCOPE tool, which can assist in gathering numerous wildcard domains, including from private bug bounty programs.
This search bar will only search within the websites you specified, making it easy to perform focused searches on those sites. For instance, if you’re searching for API endpoints, you can simply enter “api” or if you’re looking for admin endpoints, you can use relevant terms. However, this method differs from traditional Google Dorking and regular search techniques.
For more informative blogs, do visit our website regularly and stay updated with the latest insights on various topics related to cybersecurity.