In today’s digital landscape, cyber threats are continually evolving, hence cybersecurity has become an indispensable aspect of every business, regardless of its size or industry. With the ever-evolving threat landscape, organizations must prioritize proactive security measures to protect their sensitive data and systems. Two critical components of a robust security strategy are security audits and penetration testing. These assessments provide invaluable insights into an organization’s security posture, helping identify vulnerabilities before they can be exploited by malicious actors.
Understanding Security Audits
Essentially, a security audit is an in-depth examination of the information technology systems that support an organization. It evaluates the security of the system by measuring how well it conforms to a set of established criteria. It involves a systematic examination of various aspects, including network infrastructure, application security, data protection, and access controls. The primary goal of a security audit is to identify vulnerabilities and ensure compliance with security policies and regulations.
Key Components of a Security Audit
- Risk Assessment: Identifies potential threats and their impact on the organization.
- Vulnerability Assessment: Scans for weaknesses in the system that could be exploited.
- Compliance Check: Ensures that the organization adheres to relevant laws and regulations.
- Policy Review: Examines the effectiveness of existing security policies and procedures.
Types of Security Audits
- Internal Audits: Conducted by the organization’s internal security team to assess security controls and identify potential weaknesses.
- External Audits: Performed by independent third-party auditors to provide an unbiased evaluation of the organization’s security posture.
- Compliance Audits: Focus on ensuring adherence to specific industry regulations and standards, such as PCI DSS, HIPAA, or GDPR.
- Vulnerability Audits: Identify and assess system vulnerabilities that could be exploited by attackers.
Benefits of Security Audits
- Risk Identification: Uncovers potential security risks and vulnerabilities.
- Compliance Assurance: Ensure that industry regulations and standards are met and comply with the organization’s policies and procedures.
- Enhanced Security Posture: Creates a secure environment by addressing weaknesses identified by the security assessment process.
- Business Continuity: Protects critical assets and minimizes the impact of potential breaches.
- Trust Building: Demonstrates a commitment to data protection to customers and stakeholders.
The Role of Penetration Testing
Penetration testing, or pen testing, is a simulated cyber-attack on a computer system, network, or web application. It involves a systematic attempt to compromise security controls and gain unauthorized access. The purpose is to identify security weaknesses that could be exploited by real attackers. Pen testing goes beyond automated vulnerability scanning by involving human testers who think like hackers.
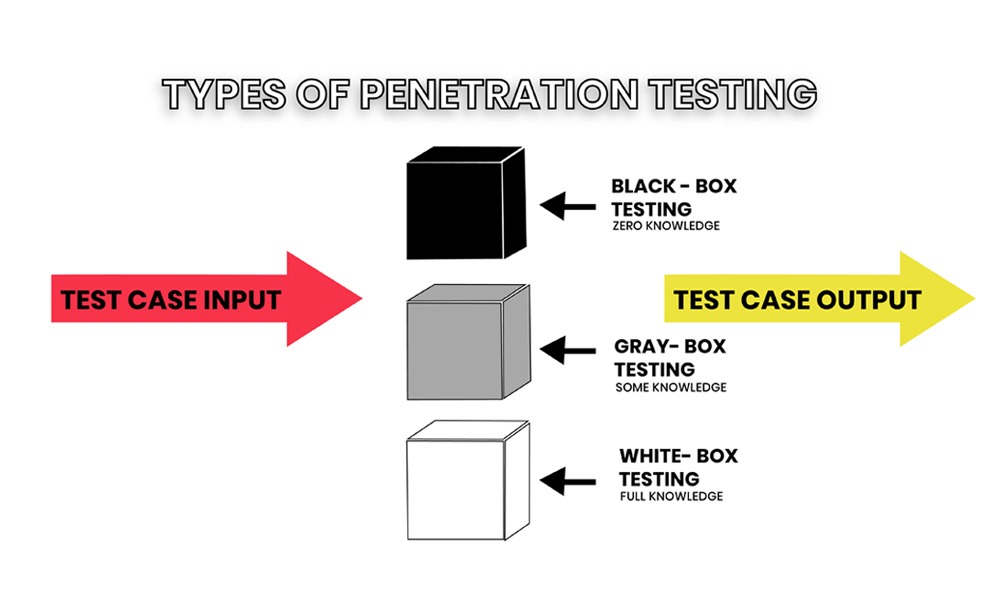
Types of Penetration Testing
- Black Box Testing: Testers have no prior knowledge of the system, simulating an external attack.
- White Box Testing: Testers have full access to the system’s information, mimicking an internal threat.
- Gray Box Testing: Combines elements of both black and white box testing, with testers having limited knowledge of the system.
Penetration Testing Methodology
Penetration testing typically follows a structured approach:
- Planning and Reconnaissance: Define the scope and objectives, gathering intelligence information about the target system.
- Scanning and Discovery: Identifying potential vulnerabilities and entry points using automated tools.
- Exploitation and Gaining access: Attempting to exploit vulnerabilities to gain access into the system.
- Post-exploitation: Testing if the vulnerability can be used to maintain a presence within the network system.
- Analysis and Reporting: Documenting findings and providing remediation recommendations.
Benefits of Penetration Testing
- Vulnerability Discovery: Determines vulnerabilities with-in the systems and applications that can be exploited.
- Threat Assessment: Evaluates the potential impact of successful attacks.
- Incident Response Improvement: Enhances the organization’s ability to respond to real-world attacks.
- Compliance Demonstration: Demonstrates compliance with security standards and regulations.
- Competitive Advantage: Builds trust with customers and partners.
Real-World Examples
Example 1: Equifax Data Breach
In 2017, Equifax experienced a massive data breach due to a vulnerability in their web application. A regular security audit could have identified this weakness before it was exploited. Penetration testing could have simulated the attack, revealing the vulnerability.
Example 2: Tesla’s Bug Bounty Program
Tesla runs a successful bug bounty program where security researchers perform penetration tests on their systems. This proactive approach has helped Tesla identify and fix vulnerabilities before they can be exploited by malicious actors.
Regular Audits and Penetration Tests! Both are crucial
Regular security audits and penetration testing are essential for maintaining a strong security posture. By combining these assessments, organizations can achieve a comprehensive understanding of their security risks and implement effective countermeasures.
Key Benefits of Combined Approach:
- Proactive Risk Management
Regular security audits and penetration testing allow organizations to identify and mitigate risks before they can be exploited. This proactive approach helps prevent data breaches and other security incidents.
- Compliance and Regulatory Requirements
Many industries have stringent security regulations. Regular audits ensure that organizations remain compliant with these standards, avoiding hefty fines and legal repercussions.
- Improved Security Posture
By identifying vulnerabilities and implementing remediation measures, organizations can strengthen their overall security posture. This makes it harder for attackers to compromise systems.
- Protecting Reputation
Organizations can suffer severe reputational damage as a result of a data breach. Regular security audits and penetration tests help maintain customer trust by ensuring the security of their data.
Best Practices for effective Security Audits and Penetration Testing
Comprehensive Security Plan
Develop a vigorous security plan defining clear objectives and scope for security drills, audits and testing.
Automated vs. Manual Testing
While automated tools are effective for identifying common vulnerabilities, manual testing by skilled professionals is essential for uncovering more complex security issues. Results are best achieved when both approaches are combined.
Collaboration and Prioritize Findings
Ensure collaboration between IT, security, and business teams. Focus on addressing critical vulnerabilities first. Develop and execute immediate remediation plans
Continuous Monitoring
Security is not a one-time effort. Continuous monitoring and regular testing help organizations stay ahead of emerging threats. Implementing security information and event management (SIEM) systems can aid in this process.
Incident Response Planning
Having a robust incident response plan is crucial. In the event of a security breach, a well-prepared response can mitigate damage and speed up recovery. Regular drills and simulations help ensure the effectiveness of these plans.
Conclusion
Regular security audits and penetration testing are no longer optional but essential components of a robust cyber security strategy. They provide a thorough assessment of an organization’s security posture, identifying vulnerabilities and ensuring compliance with regulations. By adopting these practices, organizations can proactively manage risks, improve their security measures, and protect their reputation. It is important to remember that cybercrime is an ongoing journey, and that regular assessments are key to ensuring that you stay ahead of them.
Call to Action
Protect your organization from cyber threats by scheduling regular security audits and penetration tests. Contact us today to learn more about how our comprehensive security services can help you stay secure and compliant in an ever-evolving digital landscape.
By following these guidelines and continuously improving your security practices, you can create a safer environment for your business and customers.